🛡️ WiFi Captive Portal & GDPR: The Ultimate Compliance Guide for 2026
When Guest WiFi Becomes a Legal Liability
Offering WiFi access to your customers, visitors, or residents is no longer an option: it is a standard expectation for customer experience and comfort. However, in the UK and Europe, providing a public or corporate WiFi network (even for free) comes with strict legal obligations regarding security and data protection.
At the heart of this compliance lies the WiFi Captive Portal—the authentication page that controls access to the network. Beyond being a management, security, and marketing tool, it now plays a pivotal role in compliance with the General Data Protection Regulation (GDPR) and data retention laws such as the Investigatory Powers Act 2016 in the UK.
This guide outlines the legal challenges of Guest WiFi in 2026, the best practices to adopt, and the criteria to meet to ensure your network is fully compliant.
I. Understanding the Captive Portal: More Than Just a Landing Page
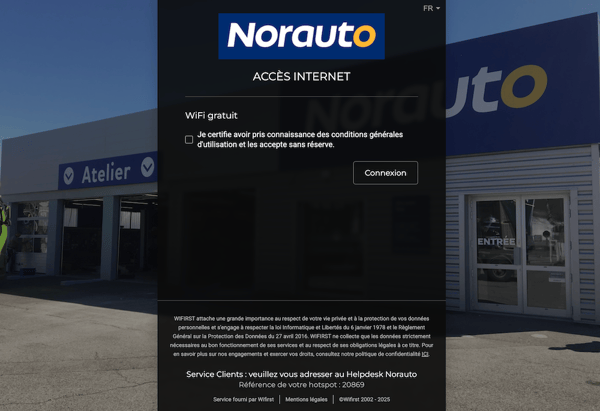
A WiFi Captive Portal is the web page that a user is automatically redirected to when attempting to connect to a WiFi network. Its primary function is to control access, but a compliant portal also fulfils three essential roles:
1. Secure Authentication
It identifies the user (via email, SMS, social login, or a unique code) and isolates each session to prevent cross-user hacking or data leakage.
2. Collecting Consent
The portal serves as the entry point to gather explicit consent from the user regarding:
- The Terms and Conditions (T&Cs) of use,
- The Privacy Policy (how their data will be used).
3. Legal Traceability
Connection data (or logs) necessary for traceability are recorded at this stage, complying with legal requirements to assist law enforcement if needed.
II. The Two Legal Pillars of Public WiFi
Any WiFi network made available to the public (customers, visitors, residents, employees) must comply with two complementary legal frameworks: Data Retention laws (anti-terrorism/crime) and Data Protection laws (GDPR).
A. Retention of Connection Logs (Investigatory Powers Act & Counter-Terrorism)
In many jurisdictions, including the UK under the Investigatory Powers Act 2016, organisations providing public internet access are often treated similarly to Internet Service Providers (ISPs) regarding data retention.
Your Obligations:
- What Data? The source IP address, the port used, the dates and times of connection/disconnection, and the MAC address of the device. Note: You generally do not record the content of communications (websites visited, emails sent), just the "who, when, and where".
- Retention Period: Typically 12 months in many European countries and the UK.
- Objective: To assist Law Enforcement Agencies (Police, Security Services) in the investigation of serious crimes or terrorism.
Risks of Non-Compliance:
- Administrative fines and potential criminal liability if you cannot provide data when served with a warrant.
- Liability for illegal activities conducted over your network (e.g., copyright infringement, illegal content) if the user cannot be identified.
B. General Data Protection Regulation (UK GDPR & EU GDPR)
Since 2018, GDPR has set the global standard for data collection and processing. As the captive portal collects personal data (emails, names, device IDs), it must adhere to strict principles.

1. Explicit and Freely Given Consent
- The user must actively agree (e.g., by ticking a box that is unchecked by default).
- WiFi access cannot be conditional on accepting marketing emails. You must offer a "connection only" option separate from the "marketing opt-in".
2. Transparency
- A clear Privacy Policy must be accessible directly from the portal login page.
- It must state:
- What data is collected,
- For what purpose (e.g., service provision vs marketing),
- How long it is stored,
- How to exercise data rights.
3. Data Subject Rights
Users have specific rights enforced by regulators like the ICO (UK) or CNIL (France):
- Right to Access, Rectification, and Erasure (Right to be Forgotten),
- Right to Object to marketing processing,
- Data Portability.
Risks of GDPR Non-Compliance:
- Fines of up to £17.5 million or 4% of total global annual turnover (whichever is higher).
- Reputational damage and loss of customer trust.
III. 2026: How to Choose a Compliant & Scalable Captive Portal
Given the complexity of these requirements, using a "free" or uncertified captive portal presents a significant legal and technical risk. A professional solution must guarantee data security, legal compliance, and a seamless user experience.
🔑 Essential Criteria for a Compliant Portal in 2026:
| Requirement | Recommended Best Practices |
|---|---|
| Log Security | Data retention for 12 months in secure, ISO 27001 certified data centres located within the UK/EU. |
| Legal Requests | A clear, established procedure to handle and respond to warrants from law enforcement. |
| GDPR Consent | "Opt-in" boxes unchecked by default; explicit statement of data usage; distinct separation between service terms and marketing consent. |
| Transparency | T&Cs and Privacy Policy must be fully visible and readable before connection. |
| User Experience | Multilingual support, responsive design (mobile-first), and accessibility compliance. |
| Data Management | Automated tools to purge data once the retention period expires or upon user request. |
IV. Complementary Best Practices
- Train your internal teams (Front Desk, IT, Marketing) on consent management and why they should never bypass the portal to give "open" access.
- Conduct an annual audit of your WiFi compliance and GDPR procedures.
- Choose a Managed Service Provider (MSP) capable of guaranteeing traceability, security, and the handling of legal requests on your behalf.
Example: The Role of a B2B Telecom Operator
Some companies, like Wifirst, act as fully registered B2B Telecom Operators. This means they take responsibility for:
- The secure legal retention of connection logs,
- Handling requests from the Police or authorities,
- Native integration of GDPR obligations (consent management, transparency, automated purging).
Partnering with such a provider can significantly simplify compliance, effectively outsourcing the legal risk—provided you verify their certifications and contractual guarantees.

Conclusion — Compliance Builds Trust
In 2026, WiFi captive portal compliance is more than just an administrative hurdle. It is a mark of trust, a brand asset, and a legal safety net.
A well-designed WiFi network—secure, transparent, and GDPR-compliant—protects not only your users but also your business reputation. Adopting a proactive approach to compliance ensures a safe, seamless, and responsible customer experience.
- Wifi (43)
- Hotel Industry (18)
- Digital Workplace (14)
- Behind the scenes (8)
- IPTV - Signage (8)
- Optical fibre (7)
- Green-IT (5)
- Retail (5)
- Education (3)
- Healthcare (2)
- Cybersecurity (1)
- General (1)
- Hospitality (1)
- PBSA (1)
- Student Accommodation (1)
- Telephony (1)
- Tips and tricks (1)
- Tourism (1)
- Wifirst (1)
You May Also Like
These Related Stories

The Essential Role of WiFi in Warehouse Operations

Revolutionizing Hotel Entertainment: Wifirst and Otrum's Connected TV Solution
